Vantage Enhances Access Controls for Managed Service Providers
Vantage announces RBAC for Managed Accounts and Inherited Permissions for Manager Users to enable granular access control.

Today, Vantage is launching two enhancements to Managed Service Provider (MSP) access controls: Role Based Access Control (RBAC) for MSP Managed Accounts, as well as inherited roles for Management Users who enter into Managed Accounts via the Management Account. These enhancements bring fine-grained access controls to child managed accounts, helping teams improve operational control and security posture.
Previously, only MSP Management Account users who had the Owner or Integration Owner role had permissions to enter Managed Accounts. These users had access to all Managed Accounts under their Management Account, and inherited the Manager User role when logging into a Managed Account through Partner Settings, which had Administrative Access to perform any action. There was no way to limit the scope of Managed Accounts a user could access, nor change the access level for a user entering a Managed Account, which limited who could be granted access to these accounts for both MSPs and their end users.
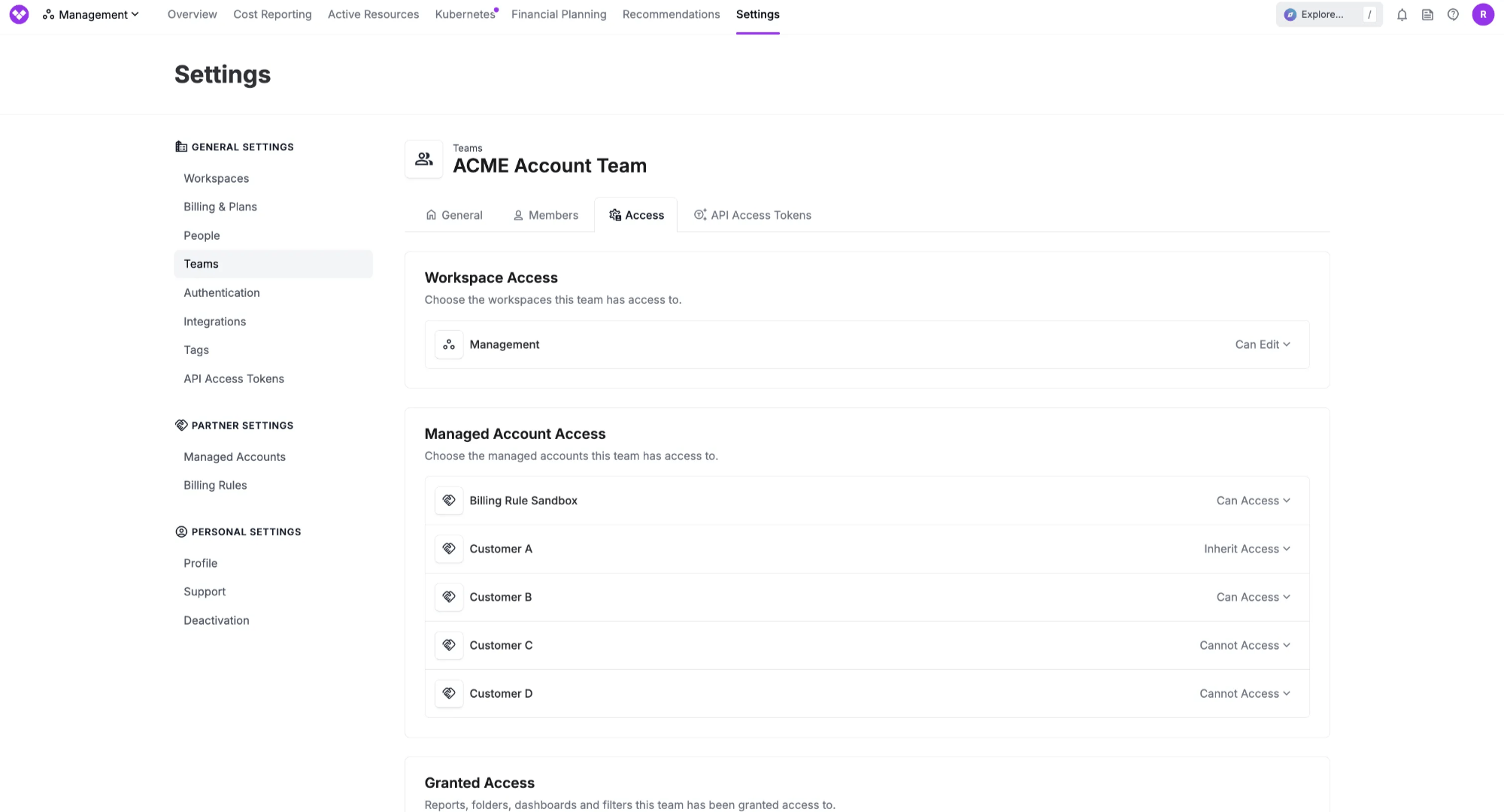
Now, Vantage MSP Customers can use RBAC to assign access to Managed Accounts through Teams. When a user is viewing the Partner Settings in the Management Account, they will now see only the Managed Accounts they have permissions to view based on the Teams they are assigned to. This allows MSP Partners to assign access based on least privilege, ensuring they can only view the costs of customers that they oversee.
Additionally, users that enter Managed Account will inherit the same role and permissions they have in the Management Account. For instance, users with the Editor role in the Management Account will now enter Managed Accounts with the same Editor privileges, giving them the ability to create reports on behalf of their customer, but restricting them from changing integration configurations or user access.
These updates are available to all Vantage MSP customers today. To get started, navigate to the Teams or Managed Accounts section in Partner Settings. Documentation is available in the MSP access control documentation.
Frequently Asked Questions
1. What is being launched today?
Vantage is releasing two new MSP access control features:
- Support for Role Based Access Control (RBAC) for Managed Accounts, enabling granular access enforcement via Teams
- Inherited permissions when Management Account users access a managed account
2. Who is the customer?
Any Vantage customer that is provisioned as an MSP account, including cloud resellers, consultancies, and FinOps service providers, looking to add permission boundaries to their Vantage account.
3. How much does this cost?
There is no additional cost for these access control features. They are included in the MSP functionality available to eligible Vantage customers.
4. How do I apply RBAC for Managed Accounts?
Users in the Management Account with the Owner role can set access to Managed Accounts by Team by:
- Navigating to the Teams tab within Settings.
- Clicking on the Team you would like to manage access for, and then click on the Access tab
- Scrolling down to Managed Account Access. Here, you will see a list of all managed accounts. Then, you can set a Team’s access to a Managed Account
5. What Access Levels can I set?
There are 3 access levels you can set for a team:
- Can Access - Members of the team will be granted explicit access to the Managed Account
- Cannot Access - Members of the team will be explicitly denied access to this Managed Account
- Inherit Access - Access to the Managed Account will be determined by the Everyone Team
6. What happens if a user has both explicit access and explicit denied access to the same workspace from different Teams they are assigned to?
If a user is a part of a Team that “Cannot Access” a Managed Account, they will not be able to access that Managed Account, even if they are given “Can Access” via a different team.
7. What role do users have when they enter a Managed Account?
Users will now maintain the same role that they have in the Management Account when entering a Managed Account.
8. Can users outside the Management Account be granted access to managed accounts?
No. Only users in the management account can be delegated access to managed accounts using this system.
9. Can I set Managed Account Access by Team through API and Terraform?
API and Terraform functionality is coming soon.
Sign up for a free trial.
Get started with tracking your cloud costs.

